- attacking every hour all devices connected to the newtwork also new device connected to guest network - detect if multiple devices are using same IPMAC - detect network cards in promiscous mode eg. Extending a wired home network.

How To Set Up A Pentesting Lab Rapid7 Blog
Todays network security experts are taking on the disguise of well-trained hackers analyzing the system to find out any potential weaknesses or loopholes to manipulate the reconnaissance strategy.

. You can then upload it to your routers settings page. OpenVAS TCP Full Scan ports 1-65535 4. If youre not running anything and all ports are closed the attack is basically done unless there is a super critical known vulnerability unpatched on your edge router the chances of getting in with no.
As they know you they might start by trying words that are familiar to you or some of the most commonly chosen passwords. First run a full scan against your home IP address. Based on your requirement you will get different results.
The Lovebox has an interesting way of accomplishing this. The main risk would be if there were known vulns or exploits for whatever game you are using. Once you connect to this network using your phone or computer you navigate to the router-page at 19216841 and input your credentials to your actual WiFi network.
The first thing they are going to do is port scan your IP address and find out what youve got running if anything. Find weak credentials with the Password Auditor 7. I would also advise on looking up a windows hardening guide and get familiar with group policy.
Bear in mind that GPO is only available on windows pro home edition doesnt have it. TCP Scanner ports 1-65535 2. I highly recommend you do a similar inspection on any device you put on your network.
Pinpoint weak configurations and common vulnerabilities with the SSLTLS Scanner 6. Those exploits would need to. Configure this computer with a static IP address that is independent of the LAN addresses used by your router.
Once you connect to this network using your phone or computer you navigate to the router-page at 19216841 and input your credentials to your actual WiFi network. First of all you can try to get a technical friend to help. A second router is also handy if you want to extend your wired Ethernet network since it grants access to additional Ethernet ports.
Its not a pentest by any means just security 101. Open source Powered by PERL Metasploit is the choice in from among the available penetration testing tools. I was wondering if there is someopensource tool avle to activelycontinously test the security of a network like.
Download Active Directory hashes of. You may need to turn on a DHCP server on the second computer so that the routers WAN interface gets an IP address as usual. When you first plug the device in and open the lid it creates a new WiFi network.
Weidman said that the next step is to test your organizations passwords and identity management capabilities. Step 2 of this network penetration testing checklist involves using this information to run tests on. See How to extend a Home Network Home Router Setup.
Lets begin shall we. Connect a second computer to the WAN port on the router. Or you can extend the Wired network by running cables into other rooms or using your power cables by installing home plug adapters.
Close open ports that dont need to be open change default or weak creds do some sort of segregation with VLANs or access lists to separate high and low critical assets. Check your printers as well if you have any which have WiFi theres a framework out there in GitHub for printer exploits look it up. Of course if youre not concerned about your wi-fi connectivity speeds an Ethernet switch is a cheaper alternative for increasing the number of Ethernet ports on your network.
Validate findings and generate pentest reports from your account. Expect to find only the ports you know you have explicitly opened open. The first thing we need to do is connect the box to a WiFi network.
If you have a normal hardware firewall and you have one port open you have no attack surface other than the game server application. First have them try to get on your system by guessing your login passwords. If you get the go ahead to perform some Pentesting on your network equipment then I would definately recommend Kali Linux or its predecessors Backtrack for pentesting - its basically a fully blown linux operating system with all kinds of exploit tools and pentesting built in I use it on my home network and perform the exploits on my test lab and ensure that it does not effect.
Learn to properly configure a firewall implement some network monitoring like an IPS. Just head to your manufacturers Support page search for your routers model number and grab the firmware update. If youre not running anything and all ports are closed the attack is basically done unless there is a super critical known vulnerability unpatched on your edge router the chances of getting in with no ports open is extremely low.
What are the steps involved in the Network Penetration Testing process also known as Network Penetration Assessments. After collecting all the information you can about your target network its time to use this information for something dicey.
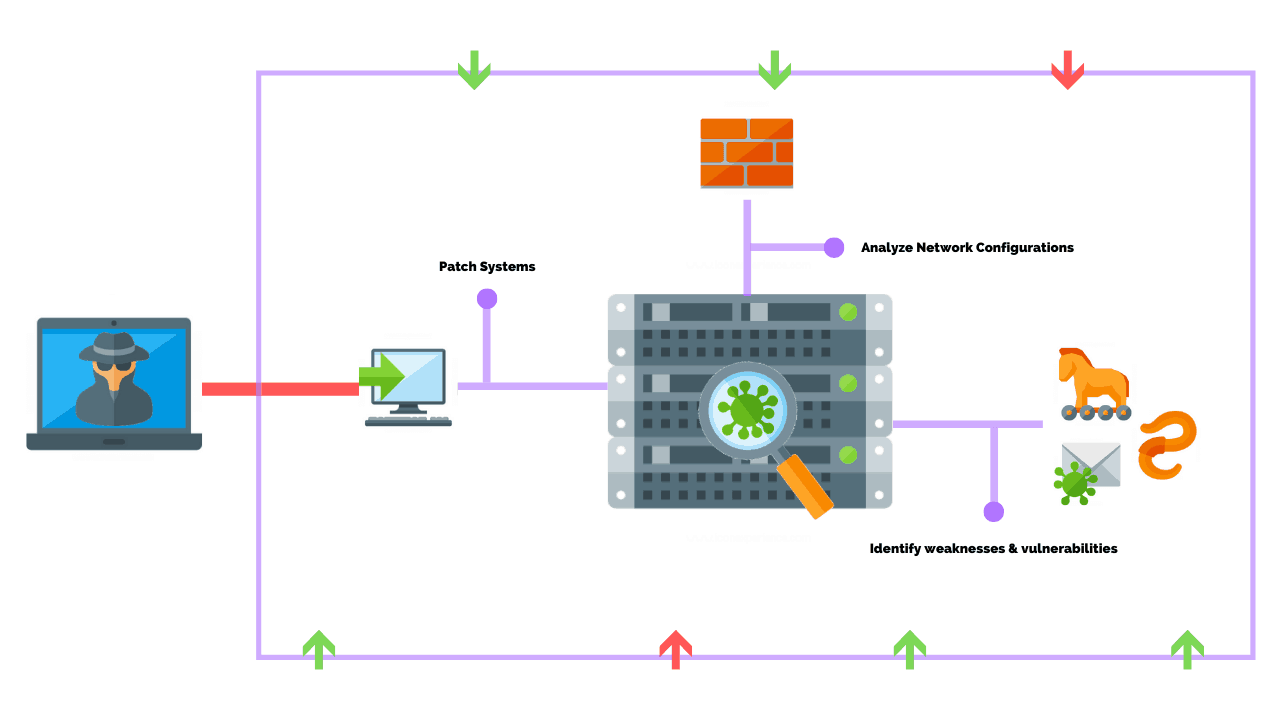
How To Perform A Successful Network Penetration Test Purplesec

Ultimate Guide On How To Perform A Successful Network Penetration Test
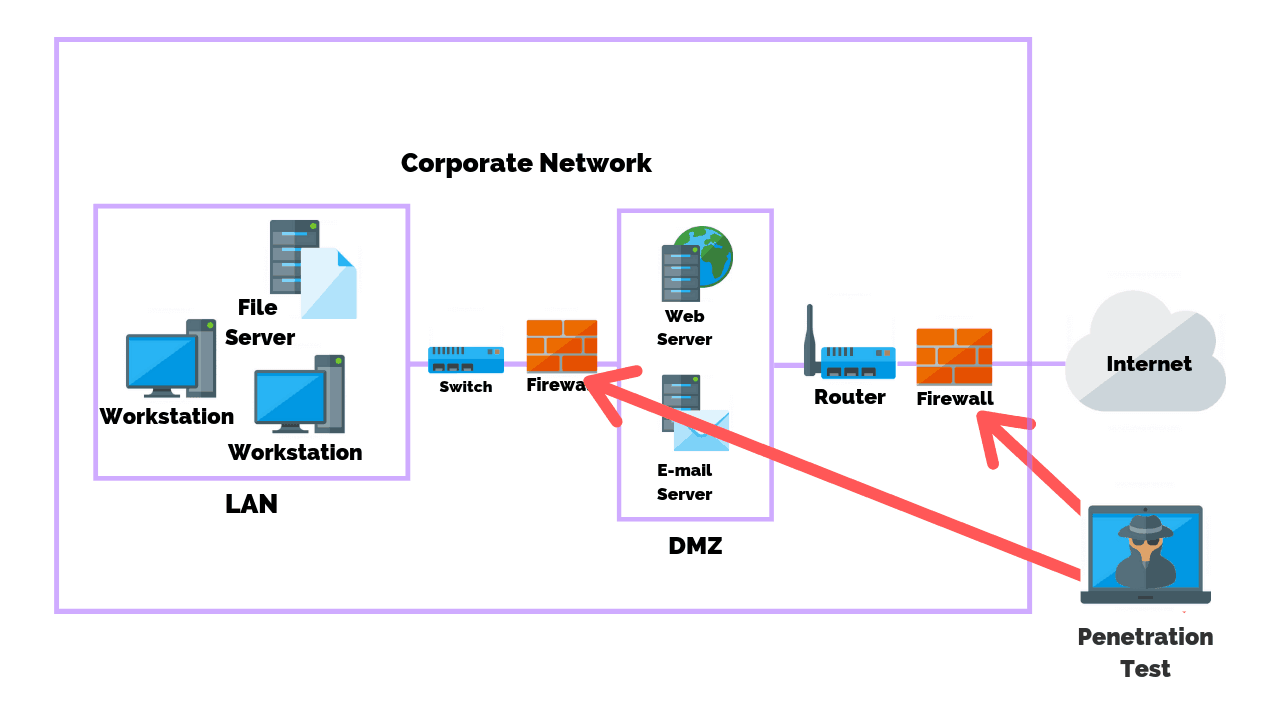
Firewall Penetration Testing Steps Methods Tools Purplesec
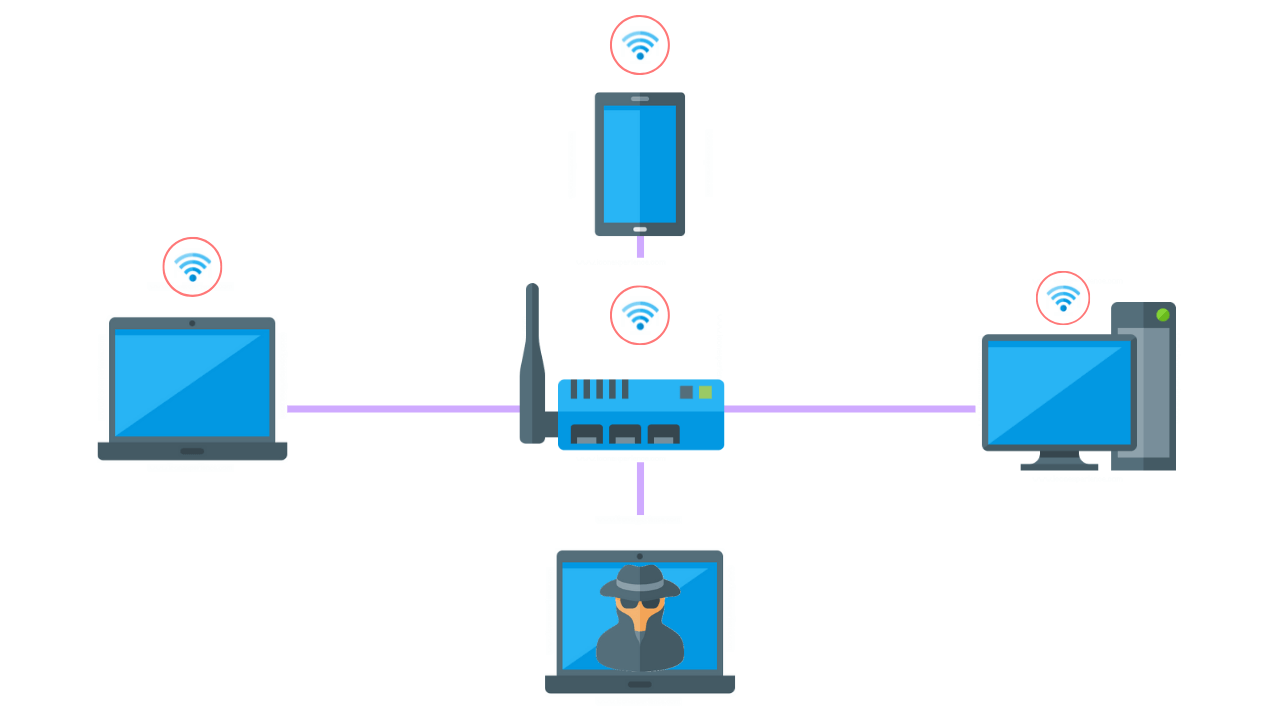
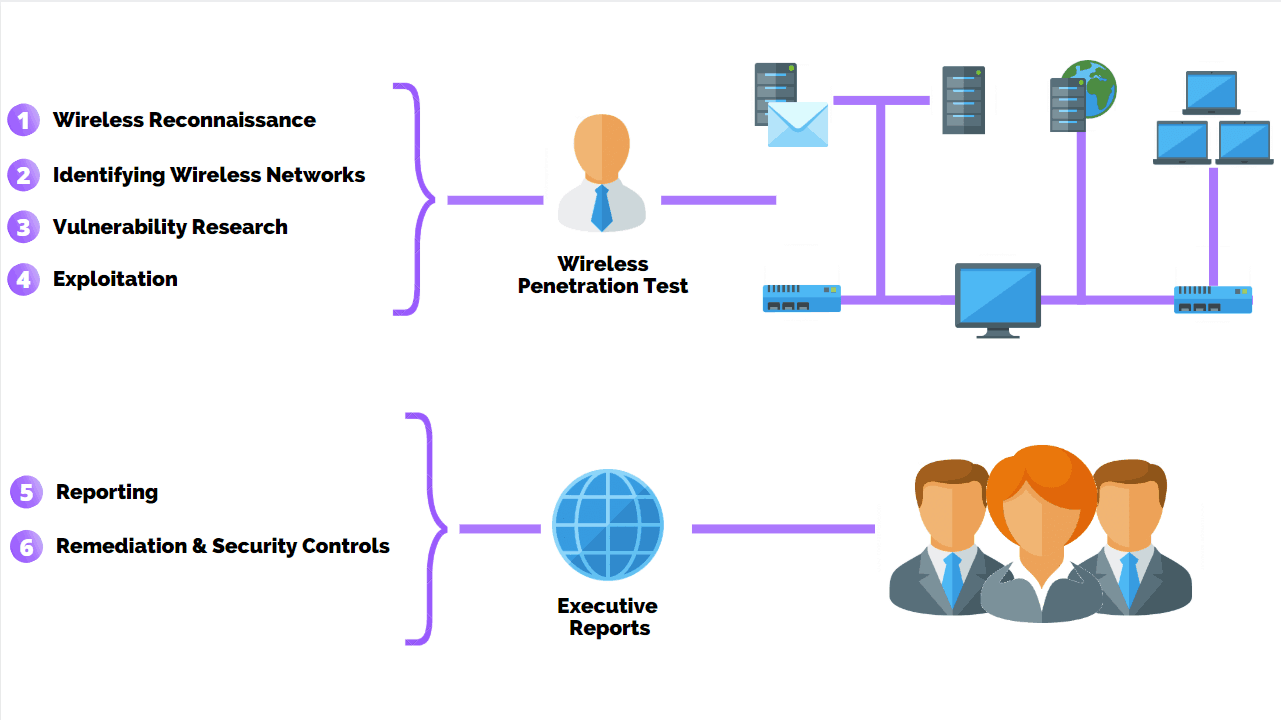
How To Perform A Successful Wifi Penetration Test
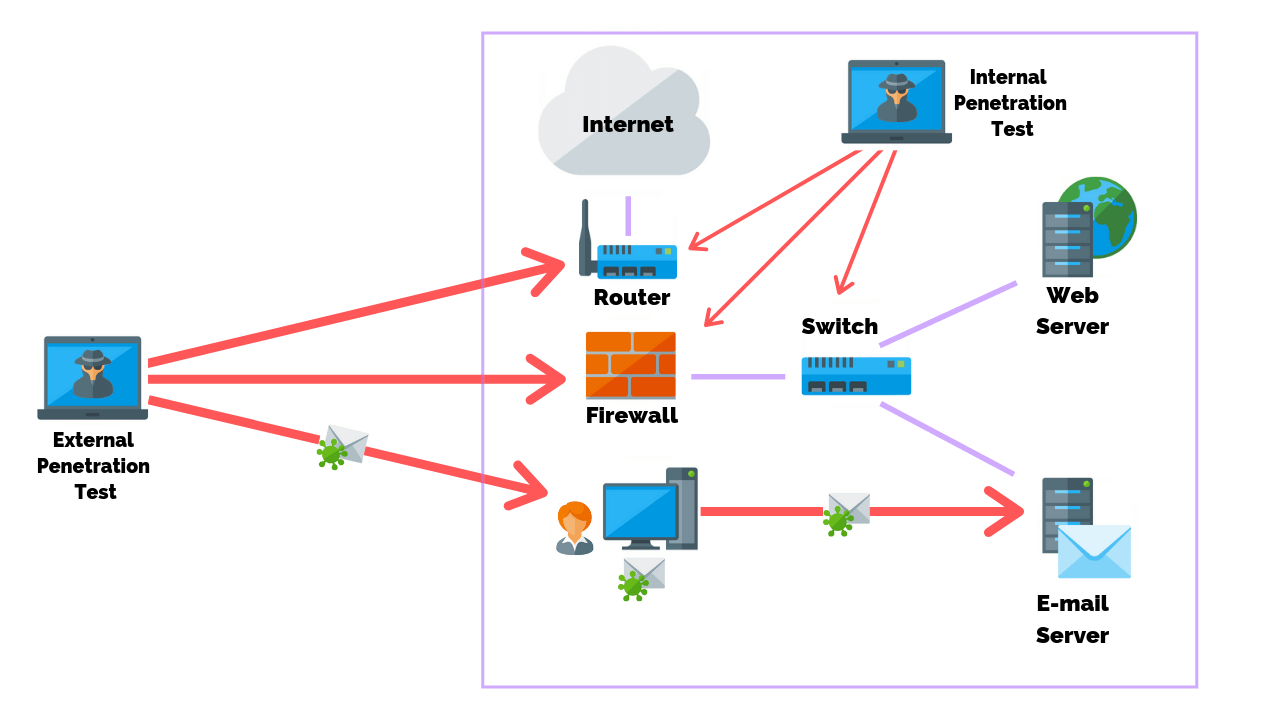
Firewall Penetration Testing Steps Methods Tools Purplesec

Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium
0 comments
Post a Comment